Fintech Payments Patent Portfolio Opportunity
TransactionsIP LLC is pleased to exclusively present the Fintech Patent Portfolio including 10 US Issued Patents, 2 US Applications, and 26 US Unpublished Applications. The Fintech portfolio is a game changing all-in-one platform to enhance and simplify the banking experience. It represents core aspects of the full fintech ecosystem. Several core patents have broad market adoption with 2005 priority dates. There are 24 Evidence of Use Charts available under an NDA.
E N D -T O – E N D F I N T E C H I P C OV E R AG E
- Cloud Wallet® • Digital Currency • Online Payments • Proximity Payments • Tokenization • Digital Coupons • Roundup Investing • Roundup Savings • Digital Receipts • Mobile Wallet • Crypto Wallet • Smartcard (fiat & Cryptocurrencies) • Wearables Payments • Digital ID • Biometric Security • Augmented Reality • And much more
The following materials are available upon request:
- Excel list of the Patent Portfolio
- Portfolio Summary, IP Revenue Roadmaps, and Detailed IP Support Materials Which are Available (under NDA).
- 2 Page Company Summary with links to 5 videos
- ModFi Company Overview
Objective is Acquisition or License to the Modfi IP Portfolio.

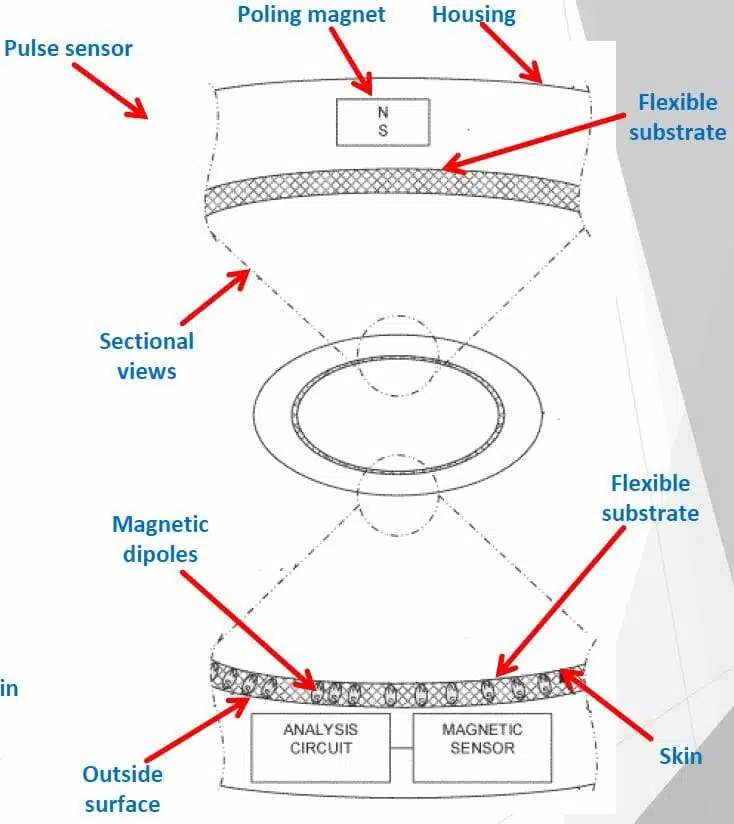 The IP relates to a heart rate monitor which includes a magnet supported to move responsive to an arterial pulse and a magnetometer configured to detect changes in a magnetic field produced by the magnet and a pulse sensor capable of measuring a pulse rate of a wearer at a peripheral artery. The technology disclosed provides the following advantages:
The IP relates to a heart rate monitor which includes a magnet supported to move responsive to an arterial pulse and a magnetometer configured to detect changes in a magnetic field produced by the magnet and a pulse sensor capable of measuring a pulse rate of a wearer at a peripheral artery. The technology disclosed provides the following advantages: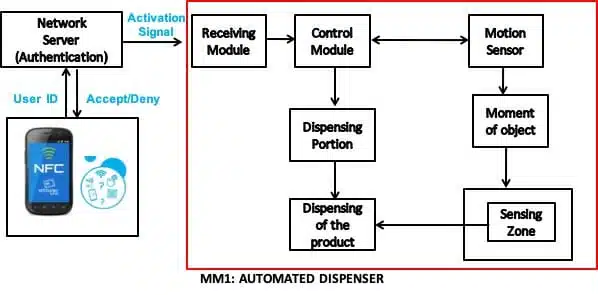 TransactionsIP LLC is pleased to present the exclusive patents for sale “ IOT AUTOMATED DISPENSER ” which includes U.S. Patents
TransactionsIP LLC is pleased to present the exclusive patents for sale “ IOT AUTOMATED DISPENSER ” which includes U.S. Patents